In Data We Trust: The “Next Gen” of Vulnerability Management
November 7, 2023
Avalor
To be effective, VM must incorporate the principles of data integrity, flexibility, and interoperability to achieve full-cycle risk assessment, ensure remediation gets done, enable dynamic reporting and dashboards.
In cybersecurity, you’ll often hear vendors claim their shiny new piece of technology will solve all of your problems. The term “next generation” or “next gen” is thrown around freely but never methodically defined. At its most basic level, next gen should mean a new approach to a known problem. In the case of vulnerability management, "next gen" means understanding the original goal and its evolution.
When it comes to VM, we've been at this work for more than 20 years as an industry, and yet very few organizations think they're doing a good job on vulnerability management. Why are traditional solutions falling short? Why are security and IT ops teams both super frustrated with VM programs? What are the key capabilities actually needed?
A quick recap on legacy vulnerability management
Security teams have been chasing the elusive goal of achieving risk-based vulnerability management (RBVM) for many years — what's the reality today?
- In today’s always-on, digital-first world, enterprises face a growing and ever-evolving threat landscape.
- Security teams use scanners (often multiple) to identify all vulnerabilities their organizations face, resulting in massive numbers of findings for security teams to parse.
- No team can remediate 100% of the found vulnerabilities. Attempting to do so would significantly delay or block the development of innovations or products that support their customers and help companies grow.
- RBVM helps security teams focus on remediating what matters most – the vulnerabilities that pose the most significant risk to the organization. Effective prioritization entails adding context to the vulnerability findings, such as business impact, threat level, and environmental factors.
- With RBVM, security teams can prioritize risk more efficiently and make the best use of their IT and developer counterparts’ time.
Sounds easy enough, right? So why hasn’t every organization successfully adopted and implemented this approach?
Historical blockers to RBVM: data challenges
The reality is that contextualizing vulnerability findings requires a host of advanced data management processes preventing teams from piecing information together, including:
- Data integration of outputs from multiple siloed sources: scanners, asset management systems, CMDBs, EDRs, threat intelligence feeds, Cloud/Application/Container/Data security platforms, SIEMs — the list goes on… all coming in different volumes and formats (API, CSV, XMP, JSON, PDF, etc).
- Data processing of massive amounts of data from the aforementioned sources. With the rise of cloud computing, security teams are facing skyrocketing amounts of data related to cloud vulnerabilities, assets, and configurations. To even begin to support this amount of data, teams need a scalable modern data architecture that can dynamically handle workloads based on size and source.
- Data normalization of inconsistent and duplicative sources.
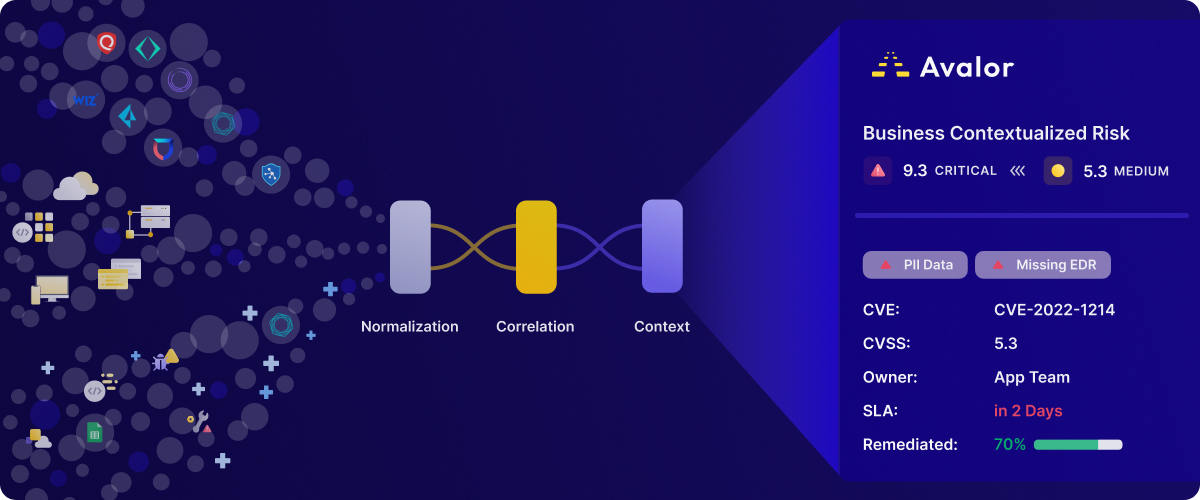
- Data enrichment to connect all of this data into a unified model – where common fields across sources (ID, asset type, CVE, etc) are reconciled so that each informs the other.
All this cross-contextualized data then needs to be put to work in:
- Business intelligence, reports, and dashboards to help stakeholders understand security metrics and objectives.
- Operational workflows for alerts, dispatch, ticketing, remediations, and patching.
Combining these data sources and activating them across teams is a complex and costly IT project — often requiring additional software and costs. This is time, budget, and data expertise that security teams don’t have today (not to mention yet another task to throw over to IT).
But now, security teams are at an inflection point — with heightened board interest in cybersecurity initiatives, increased industry awareness of the importance of data, and the evolution of security-first development practices.
The new era of vulnerability management powered by data
At Avalor, we’re empowering forward-thinking vulnerability management teams to tackle the data challenge head-on, solving three key areas:
- Building a trusted foundation of connected, enriched, and cross-contextualized vulnerability data incorporating all the valuable information generated across tools.
- Eliminating error-prone manual processes while ensuring data quality and standardized data governance.
2) Data flexibility:
- Providing a purpose-built “big data” solution for security data that helps teams maximize resources, process and store data efficiently, and dynamically execute persistent or ephemeral cloud workloads depending on the source and need.
- Measuring and tracking risk from any angle — from the individual finding and asset level to top-line product and business line views.
- Customizing risk scoring to their unique organizational needs and accounting for mitigating factors such as exposure, security controls, and threat intelligence
- Grouping findings and packaging remediation actions by criticality, supersedence, business unit, site, remediation teams, or any other business logic.
3) Data interoperability:
- Automating data-driven alerts, ownership assignment, and any operational workflows.
- Reducing organizational friction with two-way integrations with patch management and ticketing systems.
- Leveraging both pre-built and customizable risk dashboards to effectively communicate program performance for any audience, at any altitude.
Data doesn’t have to be a blocker. Instead, our philosophy is that it should be the foundation of all security programs. With Avalor, data is transformed from an impediment to the facilitator of streamlined vulnerability management across security, IT, and development teams.
Want to learn more about unlocking unified vulnerability management practices and true RBVM with automated data integrity, flexibility, and interoperability? Schedule a demo and see it for yourself!

Avalor’s AnySource™ Connector and Integrations Library: Powering Our Any Data Source, Any Format Difference
Being able to ingest some, but not all of your organization's data sources means you’re still missing a lot. In this blog post, Timna Carmel, VP of Product at Avalor, explains how the hundreds of integrations available with the Avalor platform enable enterprises to ingest, normalize, and analyze data from anywhere in the tech stack to provide full coverage of all your data.

Avalor’s Fast and Flexible Query Engine: Go Ahead, Ask Your Data Anything
Avalor CTO Kfir Tishbi explains how we built our Data Fabric for Security™ with total flexibility in mind, including the ability to set up data queries any way you like.


